Deploy Palo Alto in Azure
There are many ways to deploy Palo Alto Firewall in Azure. Out of those options today I will discuss how Palo Alto can be configured to protect your Azure workload. This setup is suitable for Proof of Concept only.
Address Space: 10.0.0.0/16
Subnet Name: Management
Subnet Address Space: 10.0.1.0/24
Subnet Name: Untrust
Subnet Address Space: 10.0.2.0/24
Subnet Name: Trust
Subnet Address Space: 10.0.3.0/24
Resource Group: PA-VNet
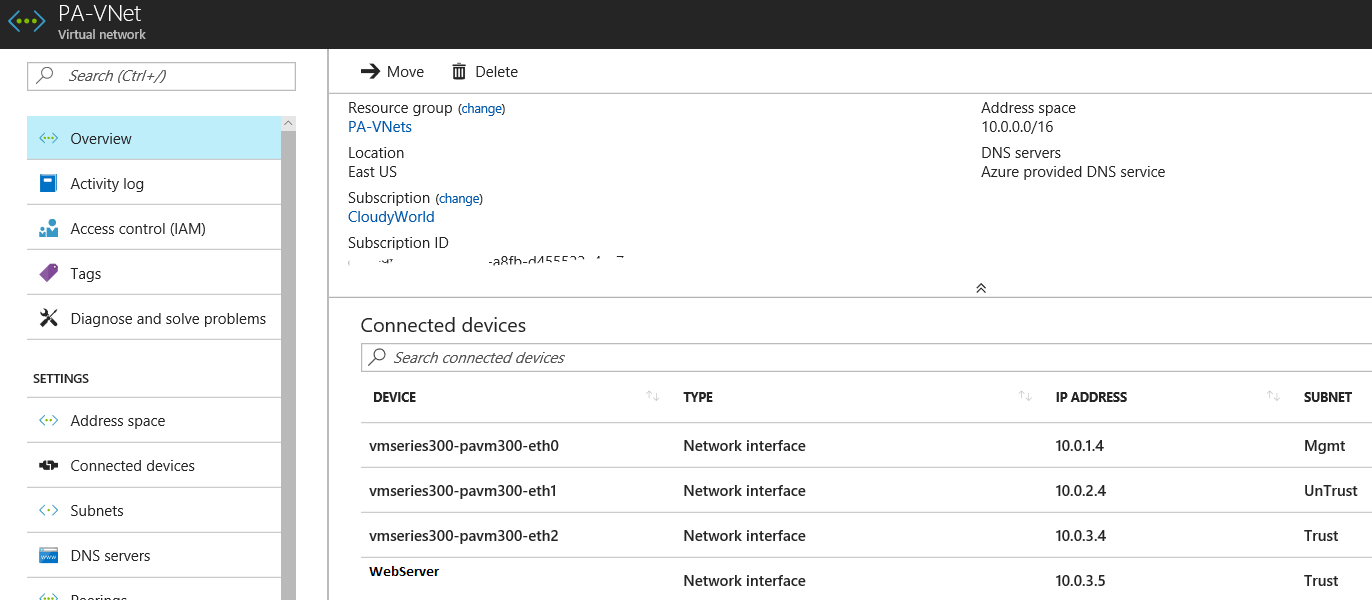
Image: Windows Server 2016
Resource Group: Services
Network: PAN-VNet
Subnet: Trust
Role: Web Server (IIS) Installed
Change NSG rules of Web Server to accept request on port 80, if you wish to test the web request. However, later on, this behaviour will be controlled through firewall.
Image: VM-Series Next Generation Firewall (BYOL)
Storage Account: PANStorage
Network: PAN-VNet
Subnet: Match with the Existing subnet
Mgmt = Mgmt
Untrust = Untrust
Trust = Trust
Assign Public IP to xxxxxx-Eth1 - Untrust Interface
Apply DefaultNSG, which had been created while deploying Firewall Virtual Machine to all interface
https://<PAFirewall VM Public address on Azure NIC eth0-Management>
Apply License: Device/Licenses/License Management and click the Activate feature using authorization code (Palo Alto Support Account is required for this)
For Ethernet1/1
Virtual Route: Default
Security Zone: UnTrust
IPv4 tab: Type: Static
IPv4 tab: Address: Private IP address assigned by Azure in CIDR notation
For Ethernet1/2
Virtual Route: Default
Security Zone: Trust
IPv4 tab: Type: Static
IPv4 tab: Address: Private IP address assigned by Azure in CIDR notation
Add Static Route
Name: Default
Destination: 0.0.0.0/0
Interface: Ethernet1/1
Next Hop Type: IP Address
Value: The UnTrust network number with a .1 (UnTrust IP: so, Value= 10.0.2.1-gateway of Untrust Subnet)
- Public IP Address assigned to UnTrusted NIC Eth1 will be used to access Web Services running inside the SecureWebService Virtual Machine
Name: SecureWebServices
Original Packet Tab > Source Zone: Untrust
Original Packet Tab > Destination Zone: Untrust
Original Packet Tabe > Destination Address: Private IP of Eth1/1
Translated Packet Tab: Translated Address: Private IP Address of SecureWebServices NIC
Name: WebServicesInbound
Source Zone: Untrust
Destination Zone: Trust
Destination Address: Private IP Address of Eth1/1
Application: ms-rdp, web-browsing
Securing Azure VNet
By default, Azure allow inbound and outbound communication with within virtual network and outbound access to the Internet. In order to control the flow of incoming and outgoing traffic from Trust Interface, we will create NSG and enforce rules.
Name: TrustedNSG
Add Inbound and Outbound Rules
This will enable unrestricted communication with the services/resources attached to 10.0.3.0/24 address space. However, it can't communicate with other subnets within the network.
Now, associate it to the WebServices NIC
Name: TrustedRouting
Click at Routes
Add the following
Route Name: DefaultviaFirewall
Address Prefix: 0.0.0.0/0
Next Hop type: Virtual Appliances
Next Hop address: Private IP of Eth1/2(Trust Interface)
Click at Subnet:
Click at Associate
Choose PaloAltoNetwork
Subnet: Trust
Now, access Web Server using the Ethernet1/1 Public IP address of the Palo Alto Firewall.
Planning-Includes Minimum Requirement - Without HA
Logical Diagram:
Create Virtual Network
Name: PAN-VNetAddress Space: 10.0.0.0/16
Subnet Name: Management
Subnet Address Space: 10.0.1.0/24
Subnet Name: Untrust
Subnet Address Space: 10.0.2.0/24
Subnet Name: Trust
Subnet Address Space: 10.0.3.0/24
Resource Group: PA-VNet

Subnet
Spin Web Server Virtual Machine
Name: SecureWebServicesImage: Windows Server 2016
Resource Group: Services
Network: PAN-VNet
Subnet: Trust
Role: Web Server (IIS) Installed
Change NSG rules of Web Server to accept request on port 80, if you wish to test the web request. However, later on, this behaviour will be controlled through firewall.
Spin Palo Alto Firewall Virtual Machine
Name: vmseries300Image: VM-Series Next Generation Firewall (BYOL)
Storage Account: PANStorage
Network: PAN-VNet
Subnet: Match with the Existing subnet
Mgmt = Mgmt
Untrust = Untrust
Trust = Trust
Assign Public IP to xxxxxx-Eth1 - Untrust Interface
Configuration of Palo Alto Firewall
Access Palo Alto Firewall via browser :https://<PAFirewall VM Public address on Azure NIC eth0-Management>
Apply License: Device/Licenses/License Management and click the Activate feature using authorization code (Palo Alto Support Account is required for this)
Create Zone
Network> Zone: Create UnTrust and Trust ZoneSetup Interface
Network>Interface:For Ethernet1/1
Virtual Route: Default
Security Zone: UnTrust
IPv4 tab: Type: Static
IPv4 tab: Address: Private IP address assigned by Azure in CIDR notation
For Ethernet1/2
Virtual Route: Default
Security Zone: Trust
IPv4 tab: Type: Static
IPv4 tab: Address: Private IP address assigned by Azure in CIDR notation
Configure Virtual Router
Network> Virtual Router and Open DefaultAdd Static Route
Name: Default
Destination: 0.0.0.0/0
Interface: Ethernet1/1
Next Hop Type: IP Address
Value: The UnTrust network number with a .1 (UnTrust IP: so, Value= 10.0.2.1-gateway of Untrust Subnet)
Configure Security and NAT for Web Server
- Public IP Address assigned to UnTrusted NIC Eth1 will be used to access Web Services running inside the SecureWebService Virtual Machine
Configure NAT
Policies>NAT- AddName: SecureWebServices
Original Packet Tab > Source Zone: Untrust
Original Packet Tab > Destination Zone: Untrust
Original Packet Tabe > Destination Address: Private IP of Eth1/1
Translated Packet Tab: Translated Address: Private IP Address of SecureWebServices NIC
Configure Security
Policy>Security> AddName: WebServicesInbound
Source Zone: Untrust
Destination Zone: Trust
Destination Address: Private IP Address of Eth1/1
Application: ms-rdp, web-browsing
Securing Azure VNet
By default, Azure allow inbound and outbound communication with within virtual network and outbound access to the Internet. In order to control the flow of incoming and outgoing traffic from Trust Interface, we will create NSG and enforce rules.
Create Network Security Group (NSG)
Name: TrustedNSG
Add Inbound and Outbound Rules
This will enable unrestricted communication with the services/resources attached to 10.0.3.0/24 address space. However, it can't communicate with other subnets within the network.
Now, associate it to the WebServices NIC
Change the Default Routes behaviour of Azure Network via Default Route
Create new Route TableName: TrustedRouting
Once deployment is completed, Open TrustedRouting Route Table.
Click at Routes
Add the following
Route Name: DefaultviaFirewall
Address Prefix: 0.0.0.0/0
Next Hop type: Virtual Appliances
Next Hop address: Private IP of Eth1/2(Trust Interface)
Click at Subnet:
Click at Associate
Choose PaloAltoNetwork
Subnet: Trust
Now, access Web Server using the Ethernet1/1 Public IP address of the Palo Alto Firewall.















Deepak,no doubt its good article but we need to accomplish Routing,NAT and Rule part as well.
ReplyDeleteKeep it up bro we are all benefiting from your research work.
Thanks,
Tanveer Bhatti
Thanks for providing for more updates on Azure Azure Online Training Bangalore
ReplyDeleteAnd still, if you going for VPN, stick to the bestvpnrating.cоm
ReplyDeleteGreat article... I followed it to the "T" and had one outstanding issue. Once I apply the DefaultviaFirewall route, my virtual servers behind the trusted interface can no longer access the Internet. Is this expected? and if so, who do you work around this issue?
ReplyDeleteOutbound NAT and security rule solved the access from the VMs to the internet.
DeleteHow does this apply to access to multiple web servers? How can we configure multiple static NATs?
ReplyDeleteIn fact we are aiming to have our external firewalls in HA behind a LB but just cannot seem to get traffic routed to the untrust interface of the fw to get to the trusted servee
This was a great article. Thanks for putting this together
ReplyDelete
ReplyDeleteThank you for sharing
Microsoft Azure Online Training
I am from a Accredited Configuration Engineer background, and now looking for a change in ACE PAN-OS 8.0. Now since do not have much knowledge of ACE Exam. Will Paloalto ACE exam help in getting a decent job? Also You can prepare yourself for the ACE questions to get ACE PAN-OS 8.0 credentials.
ReplyDeletehi sir,
ReplyDeletewhy I can't do RDP to the host in azure after do your steps ?
I only can do remotely by using anydesk :(
ReplyDeleteYou are truly an excellent webmaster. Site loading velocity is unbelievable. It sounds like you're doing a specific trick. Also, The contents are masterwork. The contents are masterwork. you’ve done a magnificent process on this topic! Turkey e visa cost is required to cover the expenses involved in processing the visa application. The amount will depend on your nationality, purpose of travel and whether you need an e-visa.
Great Post!!! thanks for it
ReplyDeleteWhy Java is Platform Independent
How Java is Platform Independent
smm panel
ReplyDeleteSmm Panel
Https://isilanlariblog.com/
İnstagram Takipçi Satın Al
hirdavatci
BEYAZESYATEKNİKSERVİSİ.COM.TR
servis
Jeton Hile
Hello everyone, If you are a citizen of Canada and you are planning a trip to Turkey. Turkish visa for Canadian citizens is available online. They can apply for a Turkey visa and enjoy a trip to Turkey.
ReplyDeleteI'm a consistent blogger, and your content is something I highly appreciate. This great article has caught my attention. I've bookmarked your site and will be checking for updates approximately once a week. I've also chosen to receive your RSS feed.Explore the Best SIM Cards For Tourists In Georgia, ensuring convenient communication and connectivity during your visit. Discover the best deals for seamless internet access in this picturesque destination.
ReplyDeleteWould you mind if I featured your posts on my blog? I promise to give full credit and cite your sources properly. Given our similar niche, I believe your content would greatly benefit my audience. Thank you for considering my request. Does a US citizen need a visa to go to Egypt? Yes, a US citizen needs a visa to travel to Egypt. However, they can obtain a visa upon arrival at Egyptian airports or apply for an e-visa before their trip. It's advisable to check the latest visa requirements and regulations before traveling.
ReplyDeleteYour blog is a sanctuary of knowledge and inspiration! Each post is a testament to your passion and expertise, offering valuable insights and practical advice. Traveling from Saudi Arabia to Australia offers a diverse experience, from the ancient wonders of Saudi Arabia to the stunning landscapes and vibrant culture of Australia. Prepare for an enriching journey filled with exploration and adventure.
ReplyDelete