Demystifying Azure Reserve Instance
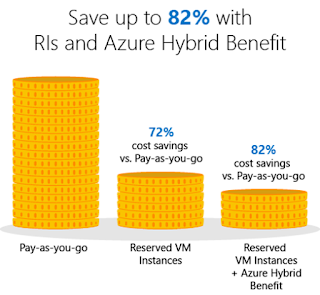
Microsoft offers numbers of ways to reduce the cost of workload running in the Azure. Initially, it started with AHUB benefits, low priority virtual machine and recently they had gone to GA of Reserve Instance. It offers huge price cut, we could save up to 72% and combined with AHUB benefits up to 82% saving can be achieved which is very luring factor for many. Source: Microsoft Off-course we all want to save money, but it comes at a cost. That cost is ‘Performance’. So, are we ready for that? Then, why Microsoft might have come up the idea of Reserve Instance? Microsoft has one of the world largest datacenters scattered throughout the world. And, those resources are not always fully utilized in some of the regions. At the same time, some regions might have been fully utilized. Thus, they allocated some portion of their resources in the Reserve Instances, and let the customer take this offer on available location based on the availability at low cost. And, most imp...