Application Security Group - Enhancement on Network Security Group
Application Security Group let us create and manage security rules for our Virtual Machine more intuitively. It provides the ability to bundle the VM's as per their workload and let us enforce rules on it as a group. So far we were applying Network Security Rules on individual VM using their IP. Now, we have the flexibility of grouping them and applying rules on them using Application Security Group name as source and destination. it eliminates the needs to remember IP address of resources.
Working with Application Security Group requires planning as we need to define the security policies. These policies are similar with Network Security Group but this features add value to Network Security Group and become more useful when you have multiple virtual machines which perform the similar works and requires same rules. If it's combined with the Tag Policy, it increases the manageability as well as increase governance.
This feature is in preview in US West Central, so we need to explicitly register it in order to take advantages of it.
Planning:
a. Let's group the VMs which have the similar nature or requires the same port to operate. As an example lets think of 3 tier architecture. Web, App and Data Tier. And, each group has number of server's.
b. Give the common name for rules - Always use the generic name for those group name. It should be meaningful. And, remember you are creating those group name not just for yourselves, how other's will respond or accept it is key to the success in long run.
c. Identify the ports that you will include in Application Security Group
d. You can include Service Tag such as Internet, VirtualNetwork, AzureLoadBalancer, AzureTrafficManager and SQL on it.
d. Create Application Security Group
e. Create NIC
f. Attached Application Security Group to newly created NIC making it member of respective group.
g. Create VM by attaching those NIC.
g. Verify if rules included in Application Security Group is applied is functional.
You can take advantage of Network Watcher tools to make sure all the rules that you want to enforce is working as expected.
PowerShell Script to create Application Security Group and applying it to the Azure Virtual Machine along with output screen.
Registration State should be Registered to move forward.
We create a Application Security Group, and attached that rule to NIC though NIC itself does not have NSG on it but we created a group and make Web Server its member thus it inherit rules from Application Security Group rules so our inbound traffic request on port 80 was entertained.
Similarly, you can validate for App Server and Database Server as well, installing appropriate server.
Working with Application Security Group requires planning as we need to define the security policies. These policies are similar with Network Security Group but this features add value to Network Security Group and become more useful when you have multiple virtual machines which perform the similar works and requires same rules. If it's combined with the Tag Policy, it increases the manageability as well as increase governance.
This feature is in preview in US West Central, so we need to explicitly register it in order to take advantages of it.
So, how to use it?
Planning:
a. Let's group the VMs which have the similar nature or requires the same port to operate. As an example lets think of 3 tier architecture. Web, App and Data Tier. And, each group has number of server's.
b. Give the common name for rules - Always use the generic name for those group name. It should be meaningful. And, remember you are creating those group name not just for yourselves, how other's will respond or accept it is key to the success in long run.
c. Identify the ports that you will include in Application Security Group
d. You can include Service Tag such as Internet, VirtualNetwork, AzureLoadBalancer, AzureTrafficManager and SQL on it.
d. Create Application Security Group
e. Create NIC
f. Attached Application Security Group to newly created NIC making it member of respective group.
g. Create VM by attaching those NIC.
g. Verify if rules included in Application Security Group is applied is functional.
You can take advantage of Network Watcher tools to make sure all the rules that you want to enforce is working as expected.
Fun Time
PowerShell Script to create Application Security Group and applying it to the Azure Virtual Machine along with output screen.
#Login to your Azure Account
Login-AzureRmAccount
#Select your subscription. Copy and paste your subscription Id
#If you have only one subscription, you can ignore this step
Select-AzureRmSubscription -SubscriptionId 'Copy Paste your subscription Id here'
#Register features
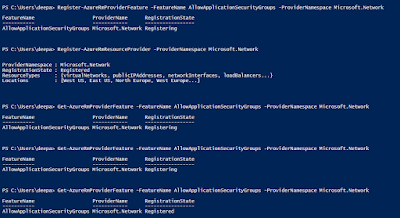
Register-AzureRmProviderFeature -FeatureName AllowApplicationSecurityGroups -ProviderNamespace Microsoft.Network
Register-AzureRmResourceProvider -ProviderNamespace Microsoft.Network
#Check the Status of the registration process.
Get-AzureRmProviderFeature -FeatureName AllowApplicationSecurityGroups -ProviderNamespace Microsoft.Network
 |
| Registration Process |
Registration State should be Registered to move forward.
#Create a new Resource Group
$RgGrpName= 'ASG'
$Loc='westcentralus'
New-AzureRmResourceGroup -Name $RgGrpName -Location $Loc
#Creating Application Security Group, Name:WebServers and assigning it to variable $WebAsg
$WebAsg = New-AzureRmApplicationSecurityGroup `
-ResourceGroupName $RgGrpName `
-Name WebServers `
-Location $Loc
#Creating Application Security Group, Name:AppServers and assigning it to variable $AppAsg
$AppAsg = New-AzureRmApplicationSecurityGroup `
-ResourceGroupName $RgGrpName `
-Name AppServers `
-Location $Loc
#Creating Application Security Group, Name:DatabaseServers and assigning it to variable $DatabaseAsg
$DatabaseAsg = New-AzureRmApplicationSecurityGroup `
-ResourceGroupName $RgGrpName `
-Name DatabaseServers `
-Location $Loc
 |
| Application Security Group created in Portal |
#Defining Web Security Rules and storing it in variable $WebRulel
$WebRule = New-AzureRmNetworkSecurityRuleConfig `
-Name "WebRule" `
-Access Allow `
-Protocol Tcp `
-Direction Inbound `
-Priority 200 `
-SourceAddressPrefix Internet `
-SourcePortRange * `
-DestinationApplicationSecurityGroupId $WebAsg.id `
-DestinationPortRange 80
#Defining Application Security Rule and storing it in a variable $AppRule
$AppRule = New-AzureRmNetworkSecurityRuleConfig `
-Name "AppRule" `
-Access Allow `
-Protocol Tcp `
-Direction Inbound `
-Priority 300 `
-SourceApplicationSecurityGroupId $WebAsg.id `
-SourcePortRange * `
-DestinationApplicationSecurityGroupId $AppAsg.id `
-DestinationPortRange 443
#Defining Database Security Rule and storing it in a variable $Database Rule
$DatabaseRule = New-AzureRmNetworkSecurityRuleConfig `
-Name "DatabaseRule" `
-Access Allow `
-Protocol Tcp `
-Direction Inbound `
-Priority 400 `
-SourceApplicationSecurityGroupId $AppAsg.id `
-SourcePortRange * `
-DestinationApplicationSecurityGroupId $DatabaseAsg.id `
-DestinationPortRange 1433
#Creating Network Security Group with Application Security Group Rules
$Nsg = New-AzureRmNetworkSecurityGroup `
-ResourceGroupName $RgGrpName `
-Location $Loc `
-Name NsgwithAppSecGrp `
-SecurityRules $WebRule,$AppRule,$DatabaseRule
 |
| WebServer Application Security Group |
 |
| All rules for 3 groups listed |
#Create Subnet configuration and associating $Nsg on it
$Subnet = New-AzureRmVirtualNetworkSubnetConfig `
-AddressPrefix 192.168.1.0/24 `
-Name Web `
-NetworkSecurityGroup $Nsg
#Creating Virtual Network - myVnet
$vNet = New-AzureRmVirtualNetwork `
-Name myVnet `
-AddressPrefix '192.168.0.0/16' `
-Subnet $subnet `
-ResourceGroupName $RgGrpname `
-Location $loc
#Creating NIC to attached to the Web Server
$Nic1 = New-AzureRmNetworkInterface `
-Name myNic1 `
-ResourceGroupName $RgGrpname `
-Location westcentralus `
-Subnet $vNet.Subnets[0] `
-ApplicationSecurityGroup $webAsg,$appAsg
#Creating NIC to attached to the App Server
$Nic2 = New-AzureRmNetworkInterface `
-Name AppNic `
-ResourceGroupName $RgGrpName `
-Location $Loc `
-Subnet $VNet.Subnets[0] `
-ApplicationSecurityGroup $AppAsg
#Creating NIC to attach to the Database Server
$Nic3 = New-AzureRmNetworkInterface `
-Name DataNic `
-ResourceGroupName $RgGrpName `
-Location $Loc `
-Subnet $VNet.Subnets[0] `
-ApplicationSecurityGroup $DatabaseAsg
# Create user object
$Cred = Get-Credential -Message "Enter a username and password for the virtual machine."
# Create the web server virtual machine configuration and virtual machine.
$WebVmConfig = New-AzureRmVMConfig `
-VMName WebServer `
-VMSize Standard_A1 | `
Set-AzureRmVMOperatingSystem -Windows `
-ComputerName WebServer `
-Credential $cred | `
Set-AzureRmVMSourceImage `
-PublisherName MicrosoftWindowsServer `
-Offer WindowsServer `
-Skus 2016-Datacenter `
-Version latest | `
Add-AzureRmVMNetworkInterface `
-Id $Nic1.Id
New-AzureRmVM `
-ResourceGroupName $RgGrpName `
-Location $Loc `
-VM $WebVmConfig
# Create the app server virtual machine configuration and virtual machine.
$AppVmConfig = New-AzureRmVMConfig `
-VMName AppServer `
-VMSize Standard_A1 | `
Set-AzureRmVMOperatingSystem -Windows `
-ComputerName AppServer `
-Credential $Cred | `
Set-AzureRmVMSourceImage `
-PublisherName MicrosoftWindowsServer `
-Offer WindowsServer `
-Skus 2016-Datacenter `
-Version latest | `
Add-AzureRmVMNetworkInterface `
-Id $Nic2.Id
New-AzureRmVM `
-ResourceGroupName $RgGrpName `
-Location $Loc `
-VM $AppVmConfig
# Create the database server virtual machine configuration and virtual machine.
$DatabaseVmConfig = New-AzureRmVMConfig `
-VMName DataServer `
-VMSize Standard_A1 | `
Set-AzureRmVMOperatingSystem -Windows `
-ComputerName DataServer `
-Credential $Cred | `
Set-AzureRmVMSourceImage `
-PublisherName MicrosoftWindowsServer `
-Offer WindowsServer `
-Skus 2016-Datacenter `
-Version latest | `
Add-AzureRmVMNetworkInterface `
-Id $Nic3.Id
New-AzureRmVM `
-ResourceGroupName $RgGrpName `
-Location $Loc `
-VM $DatabaseVmConfig
- Install IIS Role in Web Server VM
- Assign Public IP to the Web Server from the portal.
- Browse the public IP, you should able to see the IIS default home page.
- Remove Public IP from Virtual Machine once you are done with testing.
Flashback
Generally, we used to open port in NSG to allow inbound traffic at port 80. So for Web Server where applied rules?
We create a Application Security Group, and attached that rule to NIC though NIC itself does not have NSG on it but we created a group and make Web Server its member thus it inherit rules from Application Security Group rules so our inbound traffic request on port 80 was entertained.
Similarly, you can validate for App Server and Database Server as well, installing appropriate server.



Helpful blog post about application security.
ReplyDeleteMicrosoft Windows Azure Training
ReplyDeleteGood Post! Thank you so much for sharing this pretty post, it was so good to read and useful to improve my knowledge as updated one, keep blogging…!!..Azure Online Course Hyderabad