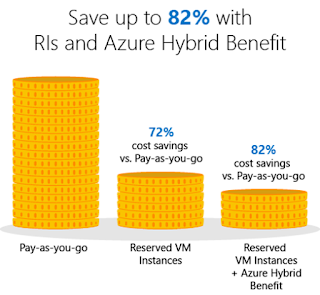
Azure Archive Storage and Blob-Level Tiering
Storage is one of the members of Infrastructure either is the cloud or in on-premises followed by Compute and Networking. Every enterprise has heavily invested in storage to store and retain data for a various compliance reason as well as to run the day to day business. And, its growth is inevitable. As of to get competitive advantages, its time to consider the Cloud offerings rather than to look for SAN and maintain it. This will result in saving time, maintenance and manpower cost with affordable operational cost. Initially, there were two-tier: Hot and Cold and new offering is Archival Storage which is added on top of Azure Storage Blob. Thus, now there are 3 storage options available for General Purpose V2(GPV2) storage account. Choosing the best tier depends on the nature of data it will be holding. Remember you are paying for storage as well as for operations performed on those datasets. Storing the frequently used data on the cold tire may result in the unexpected bills as i...